
Grafana Labs partners with GitHub to enable secret scanning
As part of our ongoing commitment to security, we are excited to announce we have partnered with GitHub to protect our users on public repositories via GitHub’s secret-scanning feature.
Through the partnership, GitHub will notify Grafana Labs when one of the following secret types is exposed in the code of a public repository:
- Grafana Service account tokens
- Grafana API keys
- Grafana Cloud API keys
- Grafana Cloud Access Policies tokens
GitHub actively monitors public repositories for leaked secrets. When a secret is detected, its hash is stored in Grafana Labs’ Secret Scanning API.
Grafana Labs’ internal services, as well as Grafana instances — whether on-premises or in the cloud — can use the API to verify whether their secrets have been made public. This verification is performed by comparing a secret’s hash with that of the exposed ones reported by GitHub.
This process is illustrated in the diagram below:
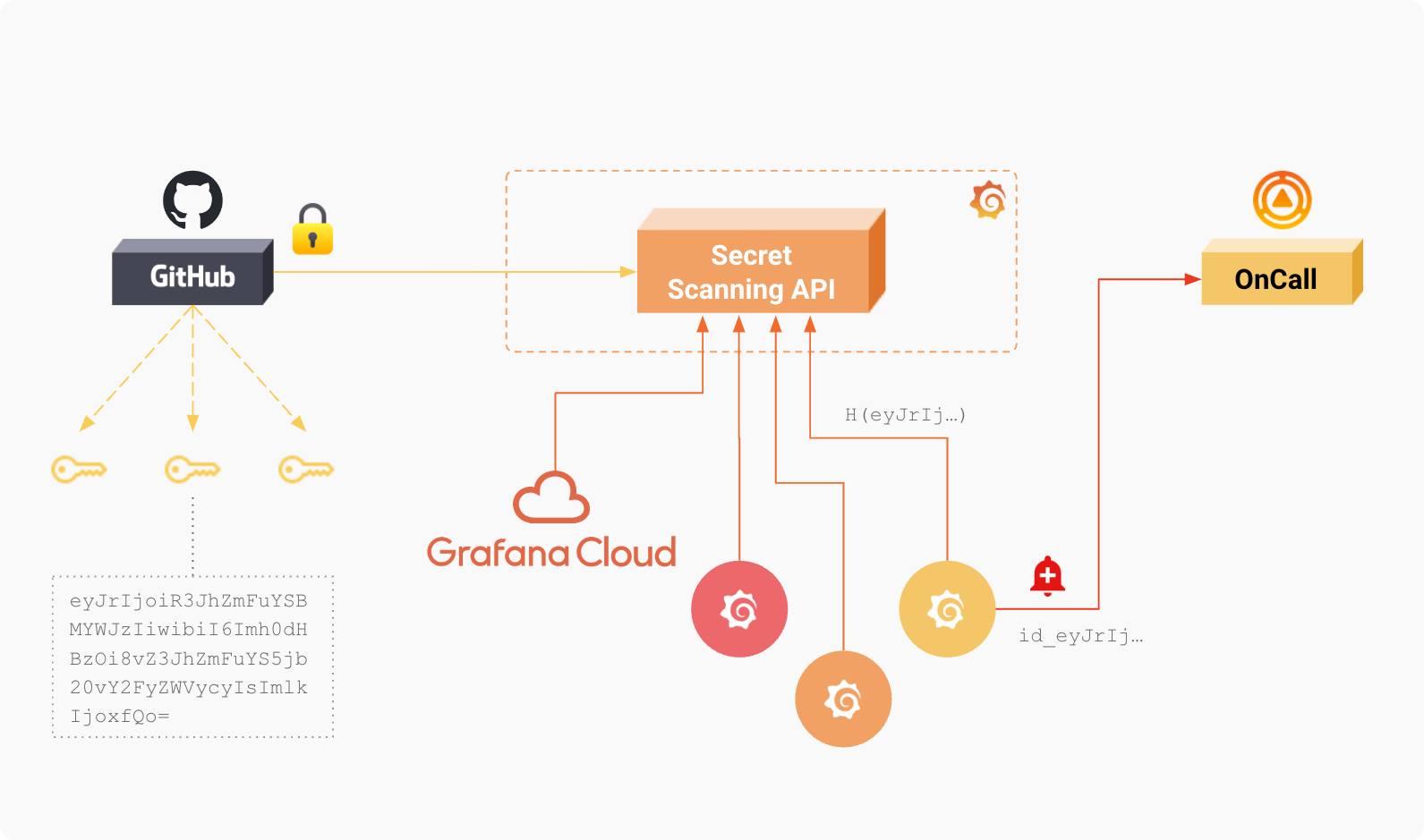
Currently, GitHub will stop most types of Grafana secrets from being pushed to public repositories, if the repository owners have enabled it. If the repository owners have not enabled push protection and a secret gets pushed, GitHub will send Grafana Labs a notification of the key that’s been leaked. Grafana Labs currently only supports automatic revocation of Grafana Service account tokens. Support for other secret types is in active development and should be rolled out soon.
Check out our documentation on Grafana secret scanning and notifications to learn how to configure automatic revocation for Grafana Service account tokens, and how to configure Grafana OnCall to promptly notify you in case of secret exfiltration.
How to enable secret scanning in Grafana
Grafana secret scanning is disabled for all instances by default, both self-hosted and on Grafana Cloud. To enable Grafana secret scanning on Grafana Cloud Pro and Grafana Cloud Advanced, reach out to Grafana Labs support and provide a valid OnCall webhook URL. To enable secret scanning for self-hosted instances, check out this documentation.
Next steps
Stay tuned as we improve the remediation flow for leaked OSS and cloud secrets — including those related to Grafana Mimir (metrics), Grafana Loki (logs), Grafana Tempo (traces), and alerting services in Grafana Cloud — to ensure you’re notified and able to act quickly.
To learn more about Grafana Labs’ recent security releases and updates — including our new bug bounty program — check out our security blog posts.



